35
loading...
This website collects cookies to deliver better user experience
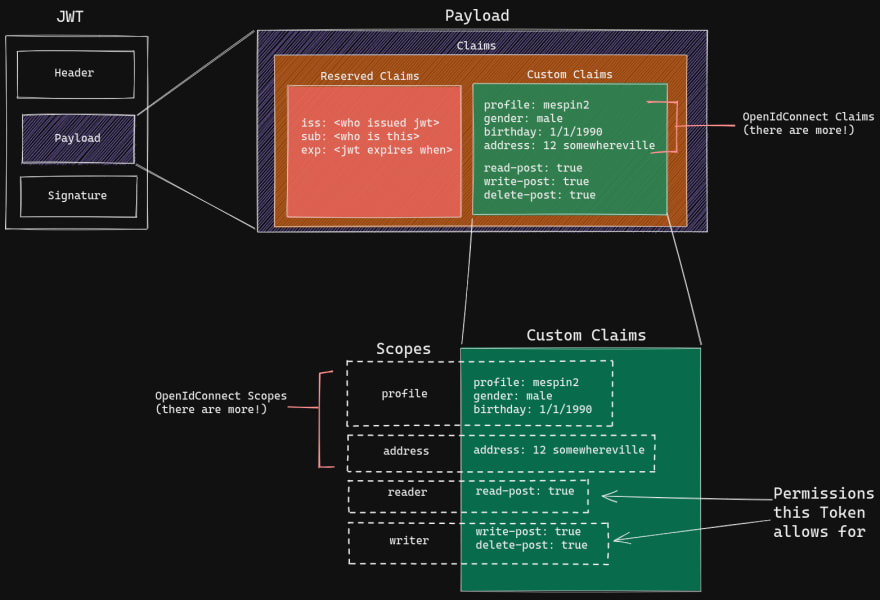
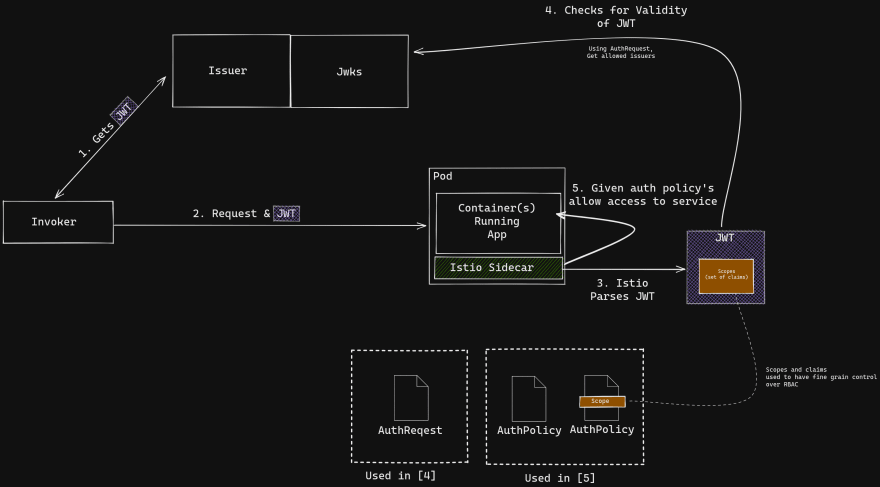
Authorization: Bearer <token> request header. There's a whole slew of tooling around doing this "handshake", from both client and server-side (Istio included). The neat thing about using a service mesh is that Istio can handle this interaction transparently to services. You only need configure the RequestAuthenication and AuthorizationPolicy objects.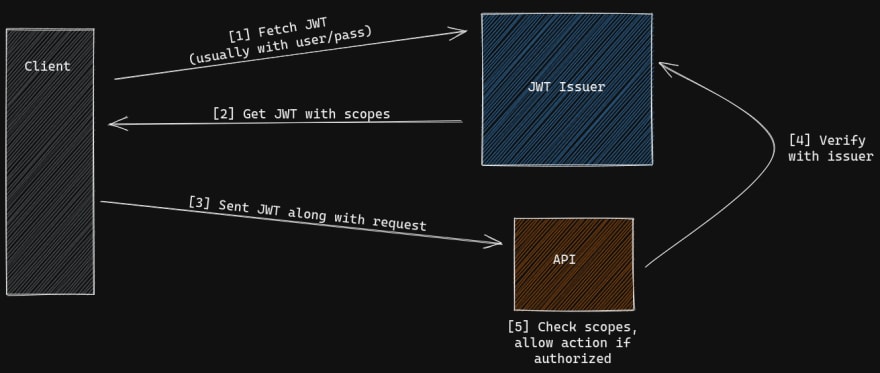
RequestAuthentication object you can specify which workloads require a JWT from which trusted issuers. Note you need to provide jwksUri so that Istio knows where to grab the certs used in the validation of the tokens (aka the JSON Web Key Set). Your issuer will have an endpoint for this (sometimes linked from the well-known endpoint ).httpbin in the foo namespace to require a valid JWT issues from google.apiVersion: security.istio.io/v1beta1
kind: RequestAuthentication
metadata:
name: foo-req-auth
namespace: foo
spec:
selector:
matchLabels:
app: httpbin
jwtRules:
- issuer: "https://accounts.google.com" # Whose JWTs do you trust?
jwksUri: "https://www.googleapis.com/oauth2/v3/certs" # Certs to verify JWTsrules, which define if certain criteria is met, what level of access is allowed.httpbin in namespace foo from any JWT (regardless of the principle) to use the GET method.apiVersion: "security.istio.io/v1beta1"
kind: "AuthorizationPolicy"
metadata:
name: "allow-reads"
namespace: foo
spec:
selector:
matchLabels:
app: httpbin
rules:
- from:
- source:
principals: ["*"]
to:
- operation:
methods: ["GET"]🚧 I will fill out this section soon. I working on more examples and diagrams to tie these concepts together!
I highly recommend reading Istio By Example for more info!
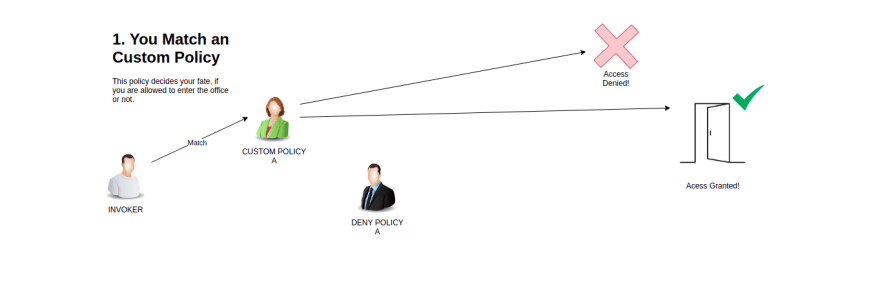
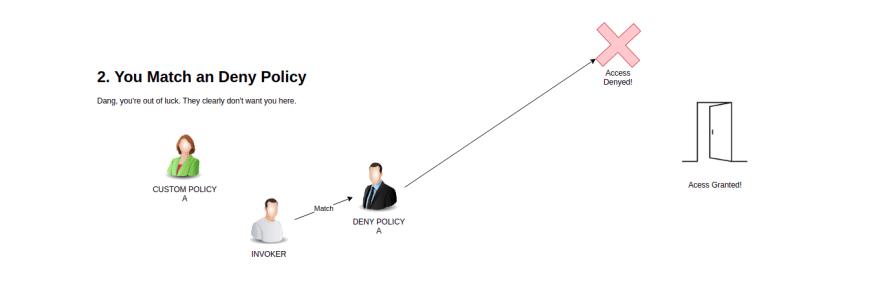
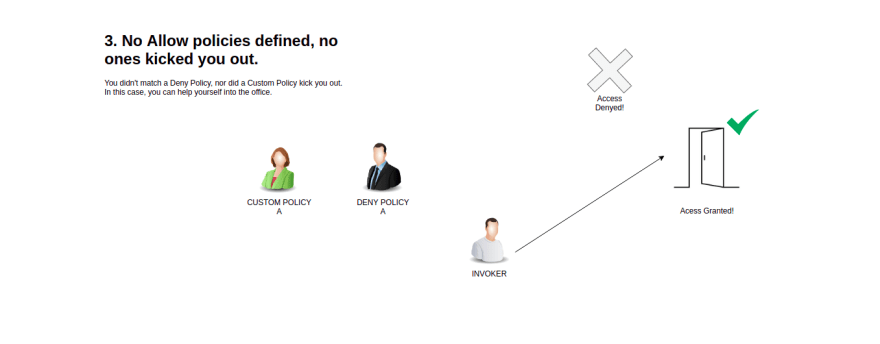
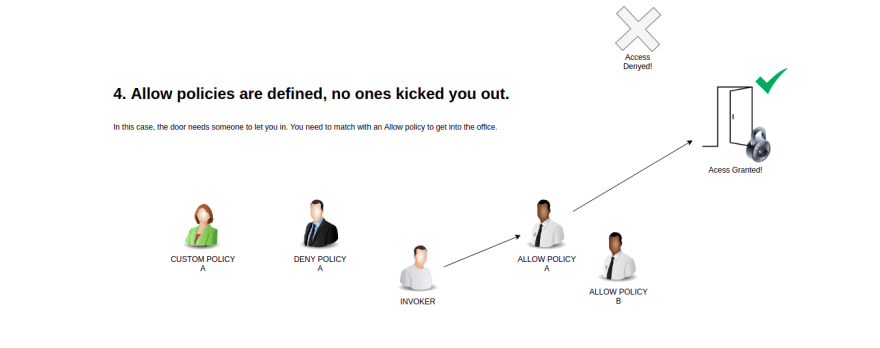
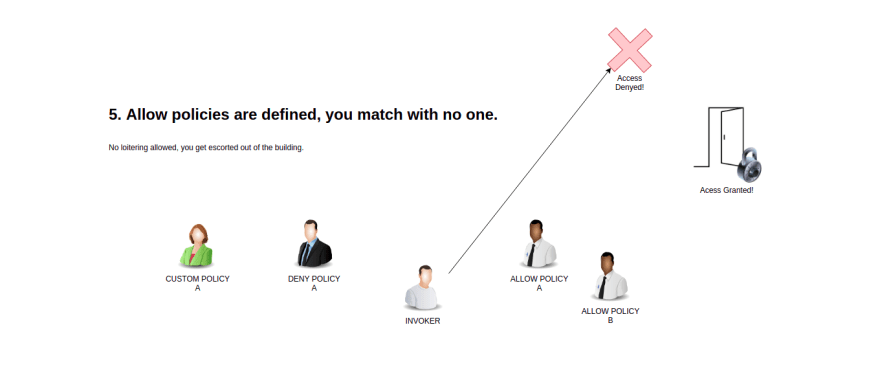
AuthorizationPolicies. Below is the flow as taken directly from the Istio documentation.1 - If there are any CUSTOM policies that match the request, evaluate and deny the request if the evaluation result is deny.
2 - If there are any DENY policies that match the request, deny the request.
3 - If there are no ALLOW policies for the workload, allow the request.
4 - If any of the ALLOW policies match the request, allow the request.
5 - Deny the request.
source
35